Introduction
Cyber-physical systems (CPS) are spreading all over the world and concern numerous applicative domains: smart grid, medical monitoring, robotics, smart farming, autonomous vehicle,… All CPS are designed around a communication backbone gathering sensors, actuators and computational resources. They are all using technologies adapted to the requirements in terms of performance, scalability, dependability, … of the applications they have been designed for. Norms and standards are emerging from these technologies, fostering the deployment of cyber physical systems.
One category of CPS gathers control command systems where the constituent devices are plugged to the electrical mains, such as smart grid, smart metering, e-mobility, public lighting, home energy management, building automation. For these types of CPS a specific communication standard has been tailored: G3-PLC. It uses power line communication technology, is hosted by the ITU standard organisation (ITU-T G.9903) and is supported by an international association, the G3-PLC Alliance, a consortium of 75+ key industrial actors. G3-PLC has been designed to be used in all countries of the world, with respect to the frequency regulations. G3-PLC is already deployed in several countries:
- Europe: France, Belgium, Luxemburg, Austria, etc.
- Middle-East: Dubaï, Saudi Arabia, etc.
- Asia: Japan, China, Taïwan, etc.
G3-PLC key features
G3-PLC offers several key features that make it a leading technology:
- As a powerline communication technology:
- G3-PLC uses the existing powerline infrastructure and therefore avoids the installation of a new infrastructure.
- G3-PLC is very efficient in dense areas, covering from the basements and underground installations to the top of the high-rise buildings.
- G3-PLC supports worldwide frequency bands, and can coexists with the existing PLC technologies.
- G3-PLC is designed for IPv6 and therefore allows a state-of-the-art and scalable network.
- G3-PLC natively offers cyber-security through the use of AES-128 cryptography.
- G3-PLC offers a robust mode that allows to operate in very harsh conditions, and even with a negative signal-to-noise ratio (i.e. when the noise is higher than the signal).
G3-PLC covers the Physical (layer 1) and Data Link (layer 2) layers of OSI model. It has been designed to be used with IPv6 at layer 3, and UDP at layer 4.
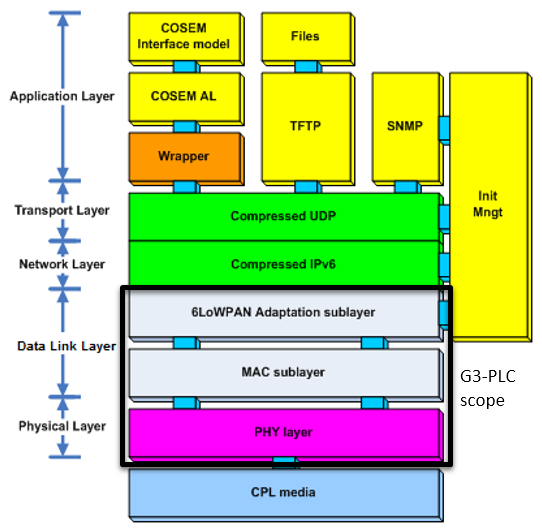
Physical layer
The physical layer is based on OFDM, with a fixed number of carriers depending on the bandplan:
| Bandplan | From (kHz) | To (kHz) | Number of carriers |
| CENELEC-A | 35.9375 | 90.625 | 36 |
| CENELEC-B | 98.4375 | 121.875 | 16 |
| FCC | 154.6875 | 487.5 | 72 |
| ARIB | 154.6875 | 403.125 | 54 |
The physical layer is made of several successive processing blocks to encode the message and add robustness using forward error correction (FEC) mechanisms:
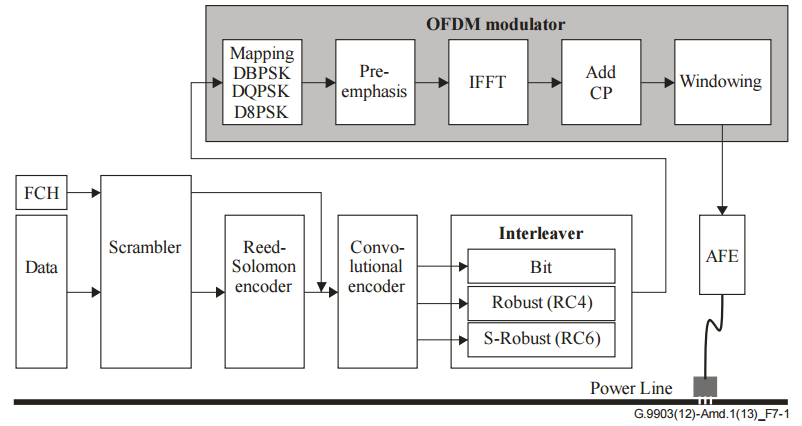
The physical layer supports differential and coherent modulations, from DBPSK/BSPK (1 bit per symbol) to D8PSK/8PSK (3 bits per symbol). An additional modulation, called ROBO, uses DBPSK/BPSK with a 4 times repetition to increase its robustness.
It also supports an adaptive tone-mapping that allows to disable some carriers for data transmission. This feature is very useful to improve the data rate and reduce the frame error rate when facing narrow-band noise or frequency-selective attenuations.
The achievable data rate at physical layer goes from ~4.5 kbps to ~234 kbps depending on the bandplan and the modulation. The most robust modulation allows to support Signal-to-Noise Ratio (SNR) down to -3 dB when facing Additive White Gaussian Noise (AWGN).
MAC Sublayer
The G3-PLC MAC sublayer is part of Data Link Layer and is based on IEEE 802.15.4.
It is responsible for:
- The access to the medium: by using CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) algorithm, it allows devices to share the PLC medium bandwidth by avoiding collisions between devices.
- The message addressing: the source and destination address allow to filter the packets that are indicated to the upper layer.
- The proper transmission of a message: it uses a CRC to check if any transmission error occurred, and manages the Automatic Repeat reQuest (ARQ) feature, that allows to acknowledge a frame (using an ACK frame) in reception and repeat the transmission in case no ACK has been received.
- The ciphering of all packets: it uses AES-CCM with a group key and allows to protect all the data exchanged between devices in network from eavesdropping or modifications. The group key configuration is under the responsibility of 6LoWPAN layer and its bootstrap procedure.
- The negotiation of the modulation and list of carriers (tone-map) to be used by the Physical layer when transmitting frame: this information is negotiated in both directions between neighbours, and stored in the Neighbour Table.
- The segmentation of the frame: it allows to adapt the size of the data provided to PHY layer to align it with the PHY MTU, which depends on the used modulation and tone-map.
Adaptation Sublayer
The G3-PLC Adaptation sublayer is part of Data Link Layer and is based on 6LoWPAN (IETF RFC 4944).
Its role is to accommodate IPv6 layer for the use on top of IEEE 802.15.4. It is responsible for:
- The fragmentation of IPv6 packets: this is required to accommodate both MAC and IPv6 constraints on Maximum Transfer Unit (MTU) values (IPv6 MTU is 1280 bytes, G3-PLC MAC MTU is 400 bytes).
- The compression of IPv6 and UDP headers: the uncompressed IPv6 and UDP headers are 48 bytes long. The Adaptation layer removes the implicit and redundant information to reduce it down to 2 bytes.
- The routing of G3-PLC packets: this feature allows to relay the frames from devices to devices in order to allow a communication between devices that are not neighbours. The discovering of the routes is performed thanks to LOADng protocol, which is defined in ITU-T G.9903 Annex D.
- The propagation of multicast frames: it is a basic flooding algorithm, in which each device relays each packet once.
- The bootstrapping: it covers the discovery and the authentication of devices willing to join the G3-PLC network. An authentication is performed using EAP-PSK protocol (defined in IETF RFC 4764), relying on a unique-per-device PSK (Pre Shared Key) which allows to authenticate the joining device and create a protected channel in which the group key (used at MAC sublayer for ciphering, see above) is provided to the device.
More info
To get more information about G3-PLC:
- G3-PLC standard is publicly available: https://www.itu.int/rec/T-REC-G.9903/
- G3-PLC Alliance maintains and supports G3-PLC standard: http://g3-plc.com/
- Trialog offers trainings about G3-PLC standard: https://www.trialog.com/en/products-and-services/training/



